
This article will not be purely Citrix related, but I really wanted to share this. I have been tasked over the years to decommission old Active Directory controllers, here and there, and if the de-promotion is usually fairly easy, and other roles migration like DHCP are also pretty much straight forward, the DNS role can be a little bit more tricky. It requires some monitoring, and the ability to generate reports for the different teams, to ask them to remove the manual DNS configuration pointing to the old AD server, which can be print servers, servers, phones, fixed workstations, kiosk machines etc.
The Tools
To generate a fancy and easy to read report with comprehensive information about who/what is still querying the DNS server, different open source tools will be used:
1. Wireshark
No need to present Wireshark. This is probably the most known packet capture tool out there. And this the one we will be using for capturing the DNS traffic. Download the package from Wireshark · Download.
Installation screen captures:
2. Nmap
Nmap is also famously known as the open source port scanner tool. This tool will be used to get information from the machines captured by Wireshark. Nmap can discover the hostname, operating systme, etc. Download the package from Download the Free Nmap Security Scanner for Linux/Mac/Windows. Note that you do not need to download and install the “npcap” library, as it is already installed by Wireshark.
3. Python
Python will be used for converting the results into Excel pivot tables. Download the package from Download Python | Python.org.
4. Nmap XML to CSV python script
Finally, an useful and well conceived script that will transform the Nmap scan result into an Excel file using pivot tables, making a clear report of who/what is still using DNS. Download the script at GitHub – NetsecExplained/Nmap-XML-to-CSV: Converts Nmap XML output to csv file, and other useful functions.
Note: Find the installation screen captures for the different tools at the end of this article.
Capture the DNS traffic (clients source IP)
Wireshark has a built-in DNS filter, making the capture a very simple and easy task. Obviously, Wireshark must be run on the DNS server itself (do I need to mention it?).
Just start Wireshark as Admin, select the active network interface (or the one used by the DNS server) and enter the following filter:
ip.dst == <your-dns-server-listening-ip> and dns
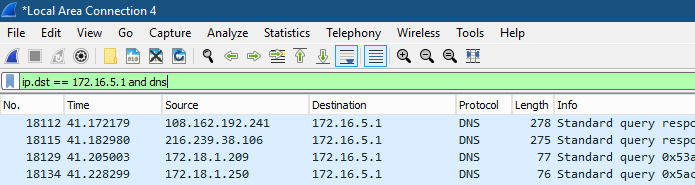
Now Wireshark is only capturing DNS traffic (in the column “Protocol”). Note that the capture, at this stage, is using the server memory (RAM). Let the capture run for an hour or two, or even for half a day, depending on your memory (RAM) availability.
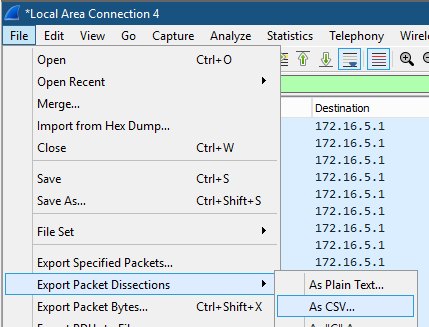
Stop the capture and then save it to CSV. Go to File > Export Packet Dissections > As CSV… .
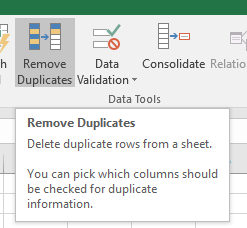
Open the CSV file in Excel and as we only need the clients source IP, delete all columns except “SOURCE“. In Excel, go to the “Data” tab and click on “Remove duplicates”.
Now we should have a single occurrence of the clients source IP addresses. Copy the list back to the server, in a text file. The text file will be saved at this location:
C:\Users\Admin\Documents\wireshark.capture.txt
Scan and ID the clients with Nmap (and view with ZenMap)
Now that we have a list of source IPs sending DNS queries to our DNS server, we will scan the list using Nmap to identify the targets. The process will be using a reverse DNS resolution and port scan to identify the hostname and operating system.
The first step is to use Nmap from the command line. Using an elevated CMD terminal (run as Admin), with the following command:
nmap -T4 -A -v -R –dns-servers 179.94.78.999 -iL “C:\Users\Admin\Documents\wireshark.capture.txt” -oX “C:\Users\Adin\Documents\nmap-output.xml”
Command line arguments explained:
– T4: Timing template, from 0 to 4. 4 is “aggressive”. Nmap could be flagged as hostile by some systems, so you may need to lower this down. Scanning will then take more time.
– A: Detect the operating system.
– v: Verbose mode.
– R: Using reverse DNS resolution, to find the hostname. You need a reverse DNS lookup zone.
– –dns-servers: Specify a DNS server with the domain zone as primary zone (with reverse lookup).
– iL: Path to the text file containing the list of IP addresses captured with WireShark.
– oX: The output file path, in XML format.
Nmap will process the IP addresses and this can take a while.
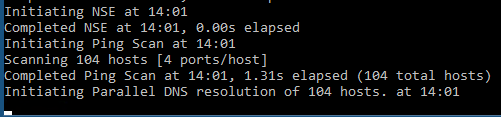
When completed, you should now get an XML file in your Documents folder. It is now possible to open the Nmap – ZenMap GUI tool to check the scan result.
Go to Scan > Open Scan. Open the XML output file. Now you should get a visual view of the hosts behind the source IPs scanned by Wireshark, with the hostname and operating system (visible with a logo):
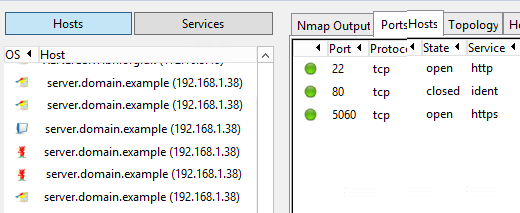
There is now enough information to identify the targets. Unfortunately, ZenMap cannot export the view to an Excel format. Which is often what we need to share the information. But a Python script is here to help us.
Export the view to Excel (Pivot Tables) with Python
Nmap – ZenMap cannot export the host scan to an Excel format, but with the “Nmap – xml2csv” python script available on GitHub, this is now possible with just a command line. Install Python on the server and downoad the script (links provided above). Then open a CMD and run:
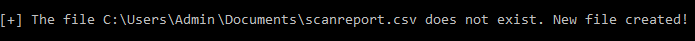
python xml2csv.py -f “C:\Users\Admin\Documents\nmap-output.xml” -csv “C:\Users\Admin\Documents\scanreport.csv”
And this is what you should get for confirmation from the script:
Great. Now it’s time to copy the CSV file on the local desktop and to fire up Excel.
In Excel you should see the columns :
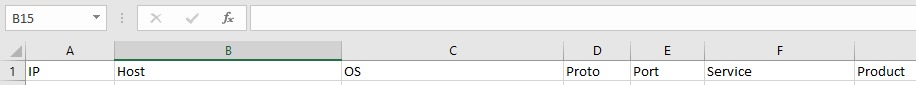
Go to “Insert” – “Pivot Table”:
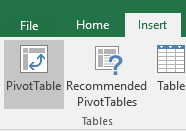
For the data input, select the first sheet with the columns and select the top columns.
For the destination just select “New Worksheet”.
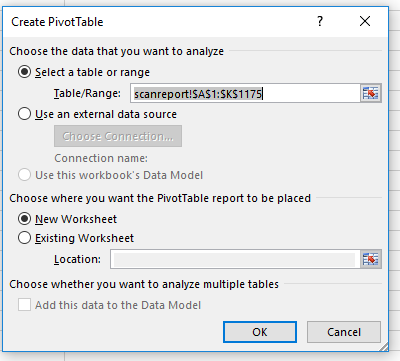
Now you can select how to arrange your new pivot table view.
Note that the order of selection is determinant. I like to select, in this order:
OS – Host – IP.
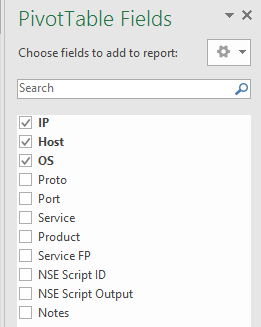
And this is the view presenting the hosts by OS, hostname, and IP:
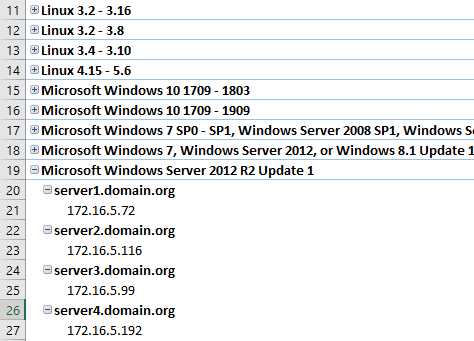
Now it is easy to locate and update the servers manually pointing to the old DNS server that we are decommissioning. A lot better than just a raw list of IPs!
Installation screen captures
Wireshark installation screen captures:
Nmap installation screen captures:
Python 3 installation screen captures:

Windows DNS server has built-in log (with IP)… just enable and parse txt